基础配置
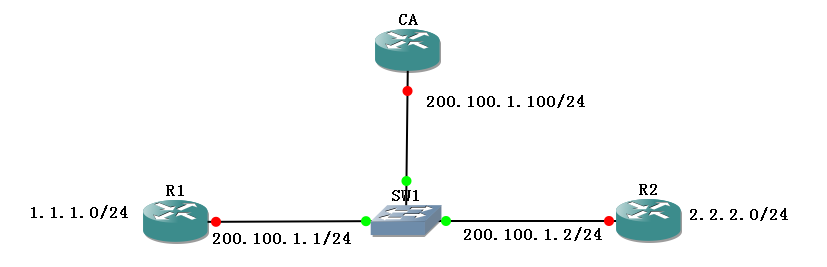
用的c7200-adventerprisek9-mz.151-4.M2.bin
- R1
conf t
int f0/0
ip add 202.100.1.1 255.255.255.0
no shu
int l0
ip add 1.1.1.1 255.255.255.0
- R2
conf t
int f0/0
ip add 202.100.1.2 255.255.255.0
no shu
int l0
ip add 2.2.2.2 255.255.255.0
- CA server
hostname CA
conf t
int f0/0
ip add 202.100.1.100 255.255.255.0
no shu
int l0
ip add 100.100.100.100 255.255.255.0
- R1
ip route 0.0.0.0 0.0.0.0 202.100.1.2
-R2
ip route 0.0.0.0 0.0.0.0 202.100.1.1
- 设置时间-3台
conf t
clock timezone GMT +8
clock set 22:00:00 Dec 24 2017
show clockcisco router架设ca服务器
conf t
ip http server
ip domain name maotai.com
crypto pki server CA
issuer-name cn=CA.maotai.com,ou=maotaisec,o=maotai,l=beijing,c=cn,e=admin@maotai.com
lifetime certificate 180
no shu
- 查看根证书(自签名证书)
show crypto pki serverr1 2生成公私钥对
conf t
crypto key generate rsa modulus 1024 label R1-key
crypto key generate rsa modulus 1024 label R2-keyr1使用sepc协议在线申请证书
- 填写到证书服务器的地址和自己的信息
crypto pki trustpoint CA
enrollment url http://202.100.1.100:80
subject-name cn=R1.maotai.com,ou=maotaisec,o=maotai
revocation-check crl- 开始提交申请
1,通过secp协议联系到了证书服务器
2,将Ca证书下载到了本地
3,将Ca证书做了hash
R1(config)#crypto pki authenticate CA #回车做了已上三件事
Certificate has the following attributes:
Fingerprint MD5: A76CA339 2E96CB3A 57B6F963 80D53D04
Fingerprint SHA1: E7128D47 37C013DB A634A016 1BD2B674 0BE48333
此时应该将ca证书的hash发给ca管理员,去核对ca证书是否是真实的. 确认后yes
- R1收到了根证书, 查看根证书
R1#show crypto pki certificates
CA Certificate
Status: Available
Certificate Serial Number (hex): 01
Certificate Usage: Signature
Issuer:
cn=CA.maotai.com
ou=maotaisec
o=maotai
l=beijing
c=cn
e=admin@maotai.com
Subject:
cn=CA.maotai.com
ou=maotaisec
o=maotai
l=beijing
c=cn
e=admin@maotai.com
Validity Date:
start date: 22:02:23 GMT Dec 24 2017
end date: 22:02:23 GMT Dec 23 2020
Associated Trustpoints: CA 3
R2操作获取CA证书-通过离线方式(不通过在线sepc协议)
crypto key generate rsa modulus 1024 label R2-key
- r2填写信息
crypto pki trustpoint CA
enrollment terminal
subject-name cn=R2.maotai.com,ou=maotaisec,o=maotai
revocation-check none
- ca导出ca证书 发给r2
R3(config)#crypto pki export CA pem terminal
% The specified trustpoint is not enrolled (CA).
% Only export the CA certificate in PEM format.
% CA certificate:
-----BEGIN CERTIFICATE-----
MIIC0zCCAjygAwIBAgIBATANBgkqhkiG9w0BAQQFADB9MR8wHQYJKoZIhvcNAQkB
FhBhZG1pbkBtYW90YWkuY29tMQswCQYDVQQGEwJjbjEQMA4GA1UEBxMHYmVpamlu
ZzEPMA0GA1UEChMGbWFvdGFpMRIwEAYDVQQLEwltYW90YWlzZWMxFjAUBgNVBAMT
DUNBLm1hb3RhaS5jb20wHhcNMTcxMjI0MTQwMjIzWhcNMjAxMjIzMTQwMjIzWjB9
MR8wHQYJKoZIhvcNAQkBFhBhZG1pbkBtYW90YWkuY29tMQswCQYDVQQGEwJjbjEQ
MA4GA1UEBxMHYmVpamluZzEPMA0GA1UEChMGbWFvdGFpMRIwEAYDVQQLEwltYW90
YWlzZWMxFjAUBgNVBAMTDUNBLm1hb3RhaS5jb20wgZ8wDQYJKoZIhvcNAQEBBQAD
gY0AMIGJAoGBAOA2917GGO8huAJ9uxfxCjlEEG3y4GyGF+oEl5tuCpWA0LncOOiI
C9l5QrheebQ/lX4bEej1ZEtfQd8IHJf/3s4VC3t0tqG0GoXIF0ESFVB8WKVQ8jam
xV5h4GHH2P3hQdaz/4lNtwxoutoHMRV2bcJXLLXDIBpx1ajp3hM2dzOvAgMBAAGj
YzBhMA8GA1UdEwEB/wQFMAMBAf8wDgYDVR0PAQH/BAQDAgGGMB8GA1UdIwQYMBaA
FBg3p/6/o/qljWcZRgBBqOtRjDXKMB0GA1UdDgQWBBQYN6f+v6P6pY1nGUYAQajr
UYw1yjANBgkqhkiG9w0BAQQFAAOBgQDGu/cxyC7uKxucQgn+vTc943O1M9mIrMn1
BMvRRYr1E9r0wtxPhfxqj6Op0A8rsvg0Y5Gufi3ePwOLOOqBAMJwb3ZfgYGLTTsv
xbLusphV3km6ooWYXWXrNqkNfJaIuZlzFdPVjc4GIVHZ/A9KPILTkB/HYZ8S2goF
JLDTdVgxgg==
-----END CERTIFICATE-----
- R2导入ca证书
R2(config)#crypto pki authenticate CA
Enter the base 64 encoded CA certificate.
End with a blank line or the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIC0zCCAjygAwIBAgIBATANBgkqhkiG9w0BAQQFADB9MR8wHQYJKoZIhvcNAQkB
FhBhZG1pbkBtYW90YWkuY29tMQswCQYDVQQGEwJjbjEQMA4GA1UEBxMHYmVpamlu
ZzEPMA0GA1UEChMGbWFvdGFpMRIwEAYDVQQLEwltYW90YWlzZWMxFjAUBgNVBAMT
DUNBLm1hb3RhaS5jb20wHhcNMTcxMjI0MTQwMjIzWhcNMjAxMjIzMTQwMjIzWjB9
MR8wHQYJKoZIhvcNAQkBFhBhZG1pbkBtYW90YWkuY29tMQswCQYDVQQGEwJjbjEQ
MA4GA1UEBxMHYmVpamluZzEPMA0GA1UEChMGbWFvdGFpMRIwEAYDVQQLEwltYW90
YWlzZWMxFjAUBgNVBAMTDUNBLm1hb3RhaS5jb20wgZ8wDQYJKoZIhvcNAQEBBQAD
gY0AMIGJAoGBAOA2917GGO8huAJ9uxfxCjlEEG3y4GyGF+oEl5tuCpWA0LncOOiI
C9l5QrheebQ/lX4bEej1ZEtfQd8IHJf/3s4VC3t0tqG0GoXIF0ESFVB8WKVQ8jam
xV5h4GHH2P3hQdaz/4lNtwxoutoHMRV2bcJXLLXDIBpx1ajp3hM2dzOvAgMBAAGj
YzBhMA8GA1UdEwEB/wQFMAMBAf8wDgYDVR0PAQH/BAQDAgGGMB8GA1UdIwQYMBaA
FBg3p/6/o/qljWcZRgBBqOtRjDXKMB0GA1UdDgQWBBQYN6f+v6P6pY1nGUYAQajr
UYw1yjANBgkqhkiG9w0BAQQFAAOBgQDGu/cxyC7uKxucQgn+vTc943O1M9mIrMn1
BMvRRYr1E9r0wtxPhfxqj6Op0A8rsvg0Y5Gufi3ePwOLOOqBAMJwb3ZfgYGLTTsv
xbLusphV3km6ooWYXWXrNqkNfJaIuZlzFdPVjc4GIVHZ/A9KPILTkB/HYZ8S2goF
JLDTdVgxgg==
-----END CERTIFICATE-----
Certificate has the following attributes:
Fingerprint MD5: A76CA339 2E96CB3A 57B6F963 80D53D04
Fingerprint SHA1: E7128D47 37C013DB A634A016 1BD2B674 0BE48333
% Do you accept this certificate? [yes/no]:
r1开始申请证书
R1(config)#crypto pki enroll CA
Dec 24 14:19:57.251: CRYPTO_PKI: Certificate Request Fingerprint MD5: 7D4A4E77 273B7C8F 17474A9A 32F6E9FB
Dec 24 14:19:57.255: CRYPTO_PKI: Certificate Request Fingerprint SHA1: 73F0386E F104BD45 13103E06 0BB3ABE3 69B5C22A
- ca颁发证书
CA#crypto pki server CA info request
CA#crypto pki server CA grant 1
R1#show crypto pki certificates
Dec 24 14:29:02.983: %PKI-6-CERTRET: Certificate received from Certificate Authority
R1#show crypto pki certificatesr2开始申请证书
- 到处自己的 个人信息+r2公钥,发给ca
R2(config)#crypto pki enroll CA
% Start certificate enrollment ..
% The subject name in the certificate will include: cn=R2.maotai.com,ou=maotaisec,o=maotai
% The subject name in the certificate will include: R2
% Include the router serial number in the subject name? [yes/no]: no
% Include an IP address in the subject name? [no]: no
Display Certificate Request to terminal? [yes/no]: yes
Certificate Request follows:
MIIBsTCCARoCAQAwUDEPMA0GA1UEChMGbWFvdGFpMRIwEAYDVQQLEwltYW90YWlz
ZWMxFjAUBgNVBAMTDVIyLm1hb3RhaS5jb20xETAPBgkqhkiG9w0BCQIWAlIyMIGf
MA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCqzJU62/bMuGxotd9cmvOQW5ftehsp
aLxQkjoE1RHgLof6KAgsRVpilNoZJJ/MMFWnJh87xyouWbU5BdHJq8zsiUT3yw9X
QOAg6goU35Av535it2J1zrYWLVL5YxtuY+iVxIt2SAjuhRdYOFyXc+qf0I3GRVAH
GI/Q5sQiMWQA0wIDAQABoCEwHwYJKoZIhvcNAQkOMRIwEDAOBgNVHQ8BAf8EBAMC
BaAwDQYJKoZIhvcNAQEFBQADgYEAKsa1DjloOMfaAqAGJ4/p/a/09IDoK9aiFSt+
RQ4Td5Dz+A+mvTBXeoUkL9hYThQvAd6h62dOh6BBLXYw10Tl3LVyodW+Dc/RSO3m
1liR8D1Ij7v9Ha94AbtfDFm2S45fi6383B/1qMmlsufcpH7r6Q1uEO0fthgo01A9
GUF8ABg=
---End - This line not part of the certificate request---
- ca导入r2的申请
CA#crypto pki server CA request pkcs10 terminal
PKCS10 request in base64 or pem
% Enter Base64 encoded or PEM formatted PKCS10 enrollment request.
% End with a blank line or "quit" on a line by itself.
MIIBsTCCARoCAQAwUDEPMA0GA1UEChMGbWFvdGFpMRIwEAYDVQQLEwltYW90YWlz
ZWMxFjAUBgNVBAMTDVIyLm1hb3RhaS5jb20xETAPBgkqhkiG9w0BCQIWAlIyMIGf
MA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCqzJU62/bMuGxotd9cmvOQW5ftehsp
aLxQkjoE1RHgLof6KAgsRVpilNoZJJ/MMFWnJh87xyouWbU5BdHJq8zsiUT3yw9X
QOAg6goU35Av535it2J1zrYWLVL5YxtuY+iVxIt2SAjuhRdYOFyXc+qf0I3GRVAH
GI/Q5sQiMWQA0wIDAQABoCEwHwYJKoZIhvcNAQkOMRIwEDAOBgNVHQ8BAf8EBAMC
BaAwDQYJKoZIhvcNAQEFBQADgYEAKsa1DjloOMfaAqAGJ4/p/a/09IDoK9aiFSt+
RQ4Td5Dz+A+mvTBXeoUkL9hYThQvAd6h62dOh6BBLXYw10Tl3LVyodW+Dc/RSO3m
1liR8D1Ij7v9Ha94AbtfDFm2S45fi6383B/1qMmlsufcpH7r6Q1uEO0fthgo01A9
GUF8ABg=
% Enrollment request pending, reqId=2
- ca为r2颁发证书,将证书发给r2
CA#crypto pki server CA grant 2
% Granted certificate:
MIIClTCCAf6gAwIBAgIBAzANBgkqhkiG9w0BAQQFADB9MR8wHQYJKoZIhvcNAQkB
FhBhZG1pbkBtYW90YWkuY29tMQswCQYDVQQGEwJjbjEQMA4GA1UEBxMHYmVpamlu
ZzEPMA0GA1UEChMGbWFvdGFpMRIwEAYDVQQLEwltYW90YWlzZWMxFjAUBgNVBAMT
DUNBLm1hb3RhaS5jb20wHhcNMTcxMjI0MTQzMDUzWhcNMTgwNjIyMTQzMDUzWjBQ
MQ8wDQYDVQQKEwZtYW90YWkxEjAQBgNVBAsTCW1hb3RhaXNlYzEWMBQGA1UEAxMN
UjIubWFvdGFpLmNvbTERMA8GCSqGSIb3DQEJAhYCUjIwgZ8wDQYJKoZIhvcNAQEB
BQADgY0AMIGJAoGBAKrMlTrb9sy4bGi131ya85Bbl+16GylovFCSOgTVEeAuh/oo
CCxFWmKU2hkkn8wwVacmHzvHKi5ZtTkF0cmrzOyJRPfLD1dA4CDqChTfkC/nfmK3
YnXOthYtUvljG25j6JXEi3ZICO6FF1g4XJdz6p/QjcZFUAcYj9DmxCIxZADTAgMB
AAGjUjBQMA4GA1UdDwEB/wQEAwIFoDAfBgNVHSMEGDAWgBQYN6f+v6P6pY1nGUYA
QajrUYw1yjAdBgNVHQ4EFgQUyjgMlXltwkGnklUtJlfoPfXtlEMwDQYJKoZIhvcN
AQEEBQADgYEArEIc54rZVAWTxb3Ve1SJulQhcJEQCO3OI1DeloSlCcpaojYq0P6t
F+ZpBnobsfEboFovOO9H4h6CSXqoo/RuoTnAiWMxJu0FnD8UC5rXk5wY8NXHX5/2
jaLBtlzhDR9aL1p9LMGb0Lj64hcvmCgWfSlqaTjDSWLNEPpcrs1GQVk=
- r2将自己的证书导入
R2(config)#crypto pki import CA certificate
Enter the base 64 encoded certificate.
End with a blank line or the word "quit" on a line by itself
MIIClTCCAf6gAwIBAgIBAzANBgkqhkiG9w0BAQQFADB9MR8wHQYJKoZIhvcNAQkB
FhBhZG1pbkBtYW90YWkuY29tMQswCQYDVQQGEwJjbjEQMA4GA1UEBxMHYmVpamlu
ZzEPMA0GA1UEChMGbWFvdGFpMRIwEAYDVQQLEwltYW90YWlzZWMxFjAUBgNVBAMT
DUNBLm1hb3RhaS5jb20wHhcNMTcxMjI0MTQzMDUzWhcNMTgwNjIyMTQzMDUzWjBQ
MQ8wDQYDVQQKEwZtYW90YWkxEjAQBgNVBAsTCW1hb3RhaXNlYzEWMBQGA1UEAxMN
UjIubWFvdGFpLmNvbTERMA8GCSqGSIb3DQEJAhYCUjIwgZ8wDQYJKoZIhvcNAQEB
BQADgY0AMIGJAoGBAKrMlTrb9sy4bGi131ya85Bbl+16GylovFCSOgTVEeAuh/oo
CCxFWmKU2hkkn8wwVacmHzvHKi5ZtTkF0cmrzOyJRPfLD1dA4CDqChTfkC/nfmK3
YnXOthYtUvljG25j6JXEi3ZICO6FF1g4XJdz6p/QjcZFUAcYj9DmxCIxZADTAgMB
AAGjUjBQMA4GA1UdDwEB/wQEAwIFoDAfBgNVHSMEGDAWgBQYN6f+v6P6pY1nGUYA
QajrUYw1yjAdBgNVHQ4EFgQUyjgMlXltwkGnklUtJlfoPfXtlEMwDQYJKoZIhvcN
AQEEBQADgYEArEIc54rZVAWTxb3Ve1SJulQhcJEQCO3OI1DeloSlCcpaojYq0P6t
F+ZpBnobsfEboFovOO9H4h6CSXqoo/RuoTnAiWMxJu0FnD8UC5rXk5wY8NXHX5/2
jaLBtlzhDR9aL1p9LMGb0Lj64hcvmCgWfSlqaTjDSWLNEPpcrs1GQVk=
% Router Certificate successfully imported
- r2查看自己的证书
R2#show crypto pki certificates
Certificate
Status: Available
Certificate Serial Number (hex): 03
Certificate Usage: General Purpose
Issuer:
cn=CA.maotai.com
ou=maotaisec
o=maotai
l=beijing
c=cn
e=admin@maotai.com
Subject:
Name: R2
hostname=R2
cn=R2.maotai.com
ou=maotaisec
o=maotai
Validity Date:
start date: 22:30:53 GMT Dec 24 2017
end date: 22:30:53 GMT Jun 22 2018
Associated Trustpoints: CA
CA Certificate
Status: Available
Certificate Serial Number (hex): 01
Certificate Usage: Signature
Issuer:
cn=CA.maotai.com
ou=maotaisec
o=maotai
l=beijing
c=cn
e=admin@maotai.com
Subject:
cn=CA.maotai.com
ou=maotaisec
o=maotai
l=beijing
c=cn
e=admin@maotai.com
Validity Date:
start date: 22:02:23 GMT Dec 24 2017
end date: 22:02:23 GMT Dec 23 2020
Associated Trustpoints: CA 配置ipsec lantolan vpn(默认使用证书认证)
- r1
ip access-list extended vpn
permit ip 1.1.1.0 0.0.0.255 2.2.2.0 0.0.0.255
crypto isakmp policy 10
crypto ipsec transform-set cisco esp-des esp-md5-hmac
crypto map cisco 10 ipsec-isakmp
match address vpn
set transform-set cisco
set peer 202.100.1.2
interface FastEthernet0/0
crypto map cisco
- r2
ip access-list extended vpn
permit ip 2.2.2.0 0.0.0.255 1.1.1.0 0.0.0.255
crypto isakmp policy 10
crypto ipsec transform-set cisco esp-des esp-md5-hmac
crypto map cisco 10 ipsec-isakmp
match address vpn
set transform-set cisco
set peer 202.100.1.1
interface FastEthernet0/0
crypto map cisco- ca吊销r2的证书
CA#crypto pki server CA revoke 0x3
% Certificate 03 succesfully revoked.
R1#clear crypto isa
R1#clear crypto sa
r1 2还是能通,为何呢?
r1有crl缓存
R1#show crypto pki crls
CRL Issuer Name:
cn=CA.maotai.com,ou=maotaisec,o=maotai,l=beijing,c=cn,e=admin@maotai.com
LastUpdate: 22:02:23 GMT Dec 24 2017
NextUpdate: 04:02:23 GMT Dec 25 2017
Retrieved from CRL Distribution Point:
** CDP Not Published - Retrieved via SCEP
CRL DER is 326 bytes
CRL is stored in parsed CRL cache
Parsed CRL cache current size is 326 bytes
Parsed CRL cache maximum size is 65536 bytes- r1清除cls缓存,强行刷新
R1(config)#crypto pki crl request CA
R1(config)#end
R1#show crypto pki crls
CRL Issuer Name:
cn=CA.maotai.com,ou=maotaisec,o=maotai,l=beijing,c=cn,e=admin@maotai.com
LastUpdate: 22:39:54 GMT Dec 24 2017
NextUpdate: 04:39:54 GMT Dec 25 2017
Retrieved from CRL Distribution Point:
** CDP Not Published - Retrieved via SCEP
CRL DER is 348 bytes
CRL is stored in parsed CRL cache
Parsed CRL cache current size is 674 bytes
Parsed CRL cache maximum size is 65536 bytes- 再次测试发现不同了
R1#clear crypto isa
R1#clear crypto sa
R1#ping 2.2.2.2 so lo0 re 1000
Type escape sequence to abort.
Sending 1000, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
Dec 24 14:42:53.619: %CRYPTO-5-IKMP_INVAL_CERT: Certificate received from 202.100.1.2 is bad: CA request failed!.
Dec 24 14:42:53.623: %CRYPTO-6-IKMP_MODE_FAILURE: Processing of Main mode failed with peer at 202.100.1.2.
Dec 24 14:42:55.207: %CRYPTO-4-IKMP_BAD_MESSAGE: IKE message from 202.100.1.2 failed its sanity check or is malformed.解决缓存
1, ocrl 在线获取crl(思科ios不支持)
2, 本地不缓存
R1(config)#crypto pki trustpoint CA
R1(ca-trustpoint)#crl cache none 




















 548
548











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








